Reading Azure Key Vault Secret from Azure Function using Managed Identity
Overview
Managing secrets, keys, certificates, and credentials is always challenging for developers. Managed identities provide an effective way to overcome managing these for them.
In this article, we are going to explore one such scenario of reading Azure Key Vault Secret from Azure Function using Managed Identity.
Azure Function
Let us start with creating an Azure function.
From the Azure portal, create a Function app as follows:
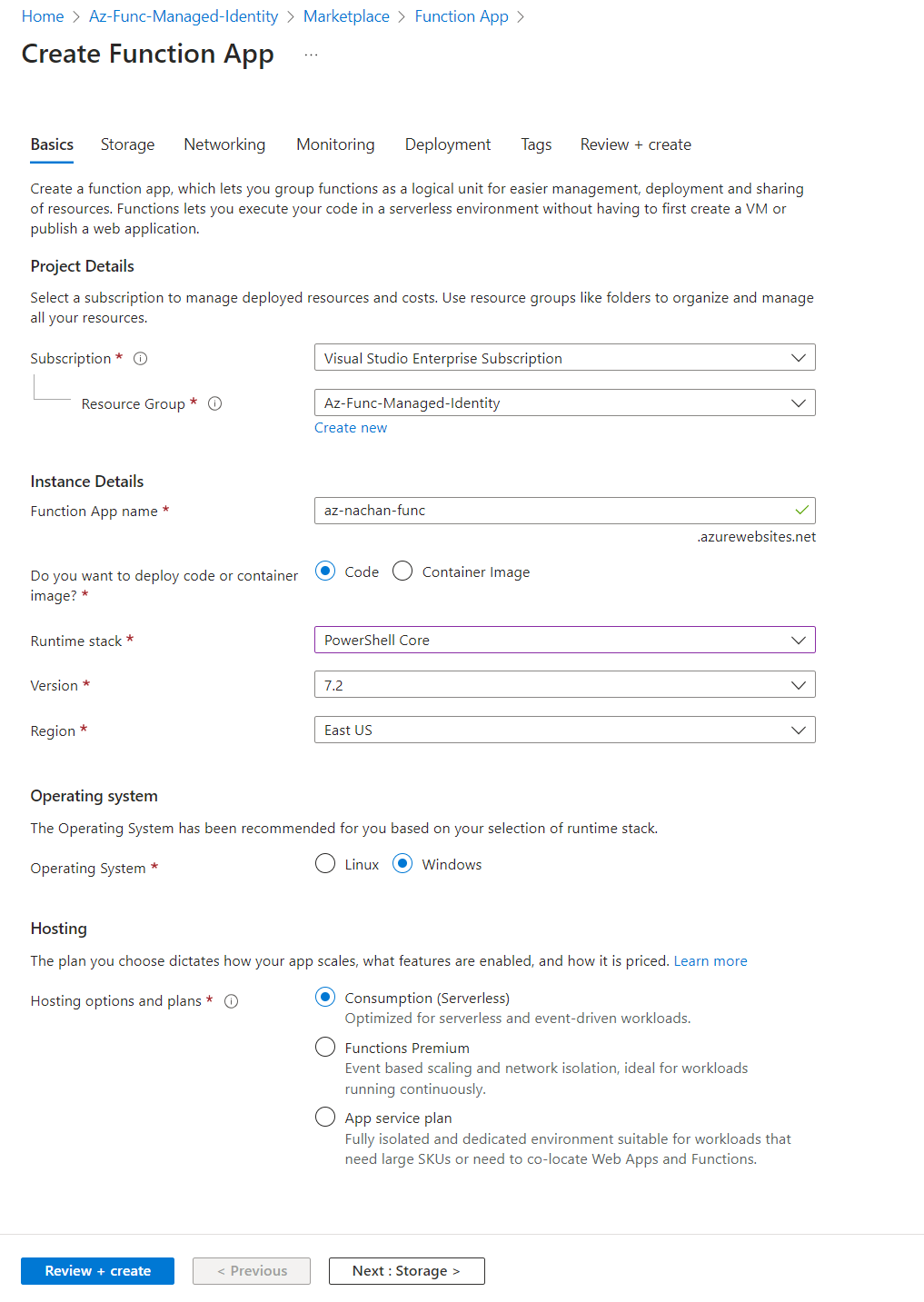
In the Function app, let us create an HTTP trigger-based function with an Authorization level as a Function to read the configuration values from the Application settings.
Store the Application Settings
Follow the below steps to store the application settings, which we will read from the Azure function later:
- In the Azure Function app, under Settings click Configuration.
- Under Application settings, click + New application setting.
-
Create a new application setting as follows:
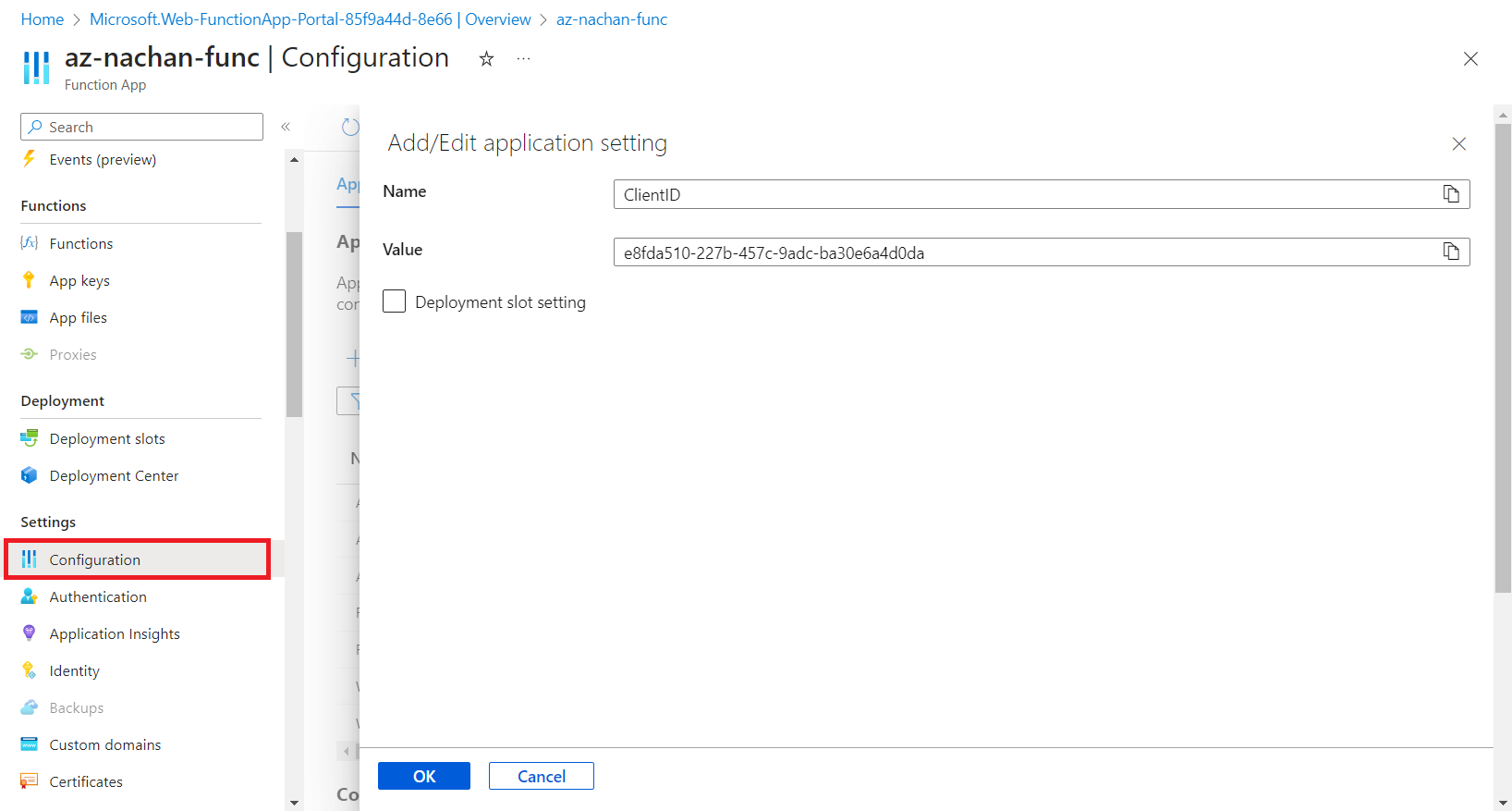
- Click Save.
Read application settings from the Azure Function
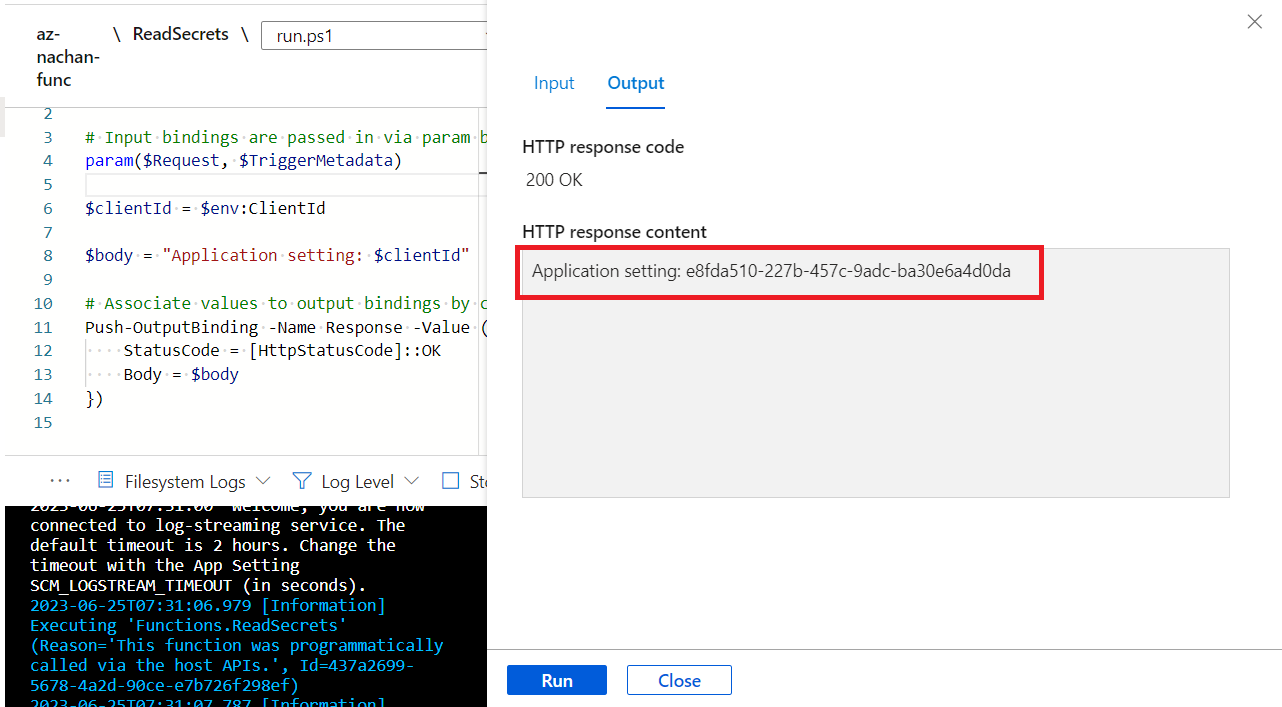
Write below code the Azure function to read the application setting:
using namespace System.Net
# Input bindings are passed in via param block.
param($Request, $TriggerMetadata)
$clientId = $env:ClientId
$body = "Application setting: $clientId"
# Associate values to output bindings by calling 'Push-OutputBinding'.
Push-OutputBinding -Name Response -Value ([HttpResponseContext]@{
StatusCode = [HttpStatusCode]::OK
Body = $body
})
Run the function to verify that it correctly reads the Application setting.
Azure Key Vault
Instead of maintaining the configurations at an individual resources (e.g., Azure Function) level, it is always a good idea to maintain them at a single location, i.e., Azure Key Vault.
From the Azure portal, create a key vault as follows:
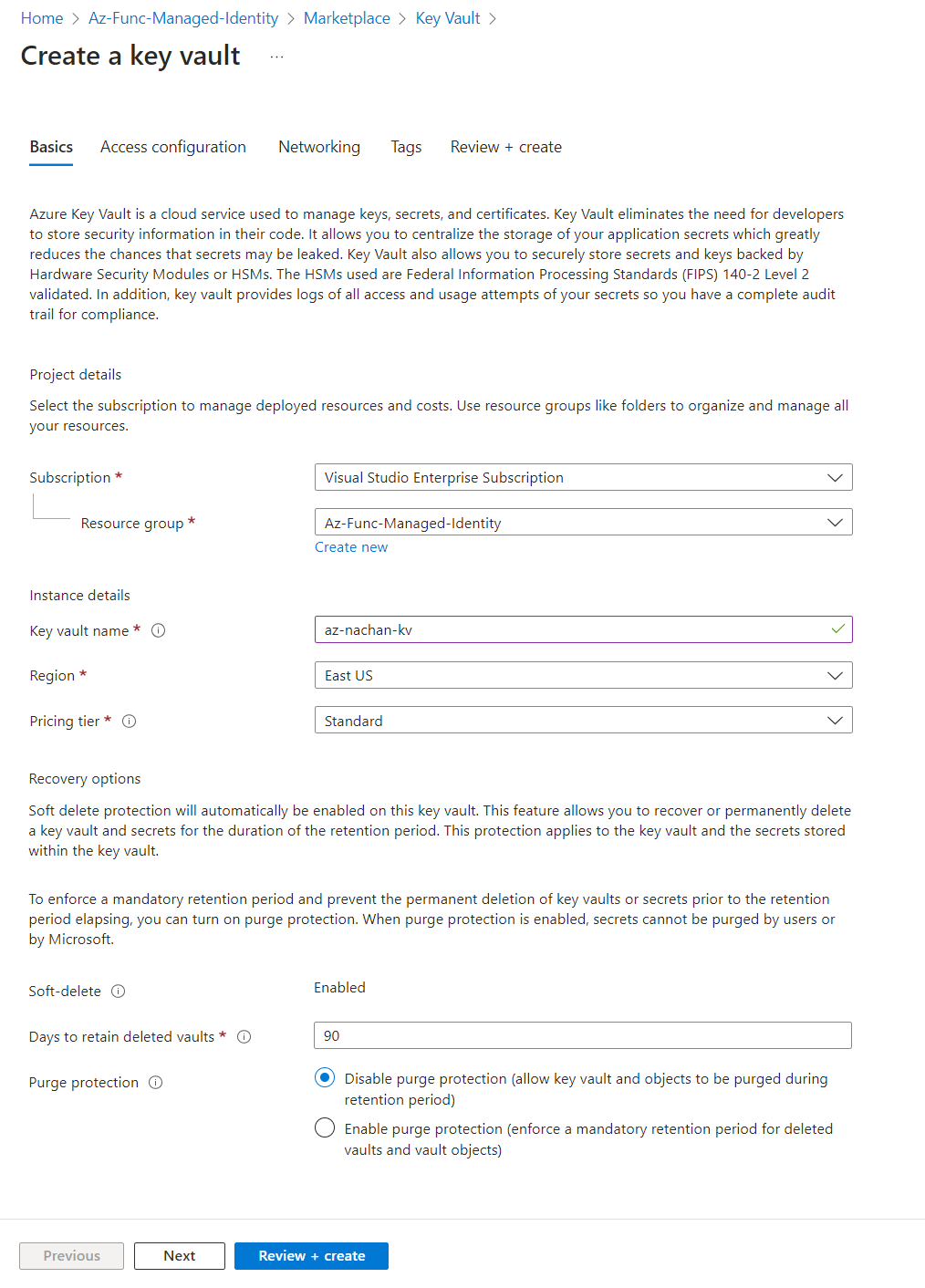
Once the key vault is ready, create a secret by navigating to the Secrets option under Objects.
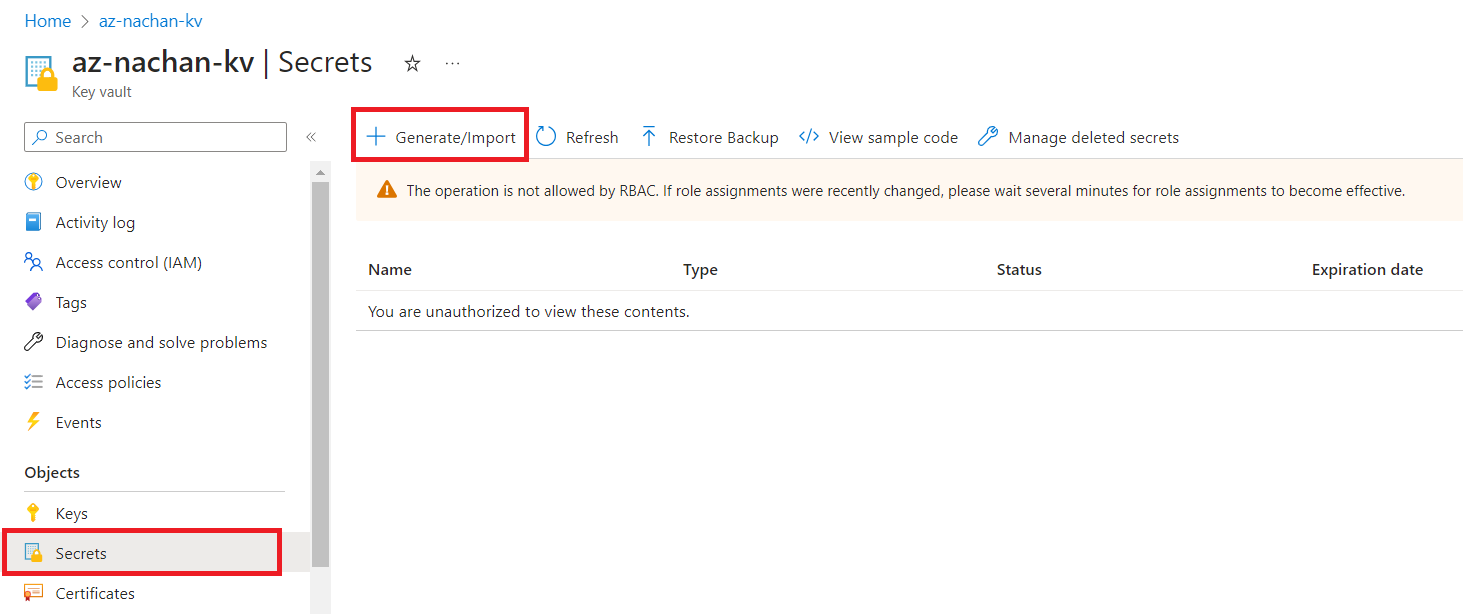
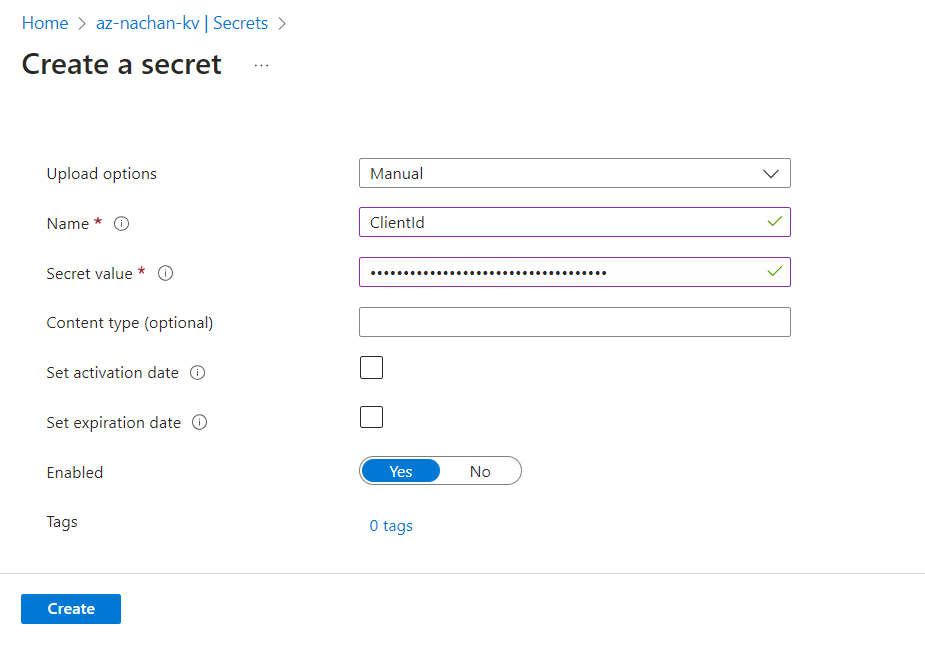
Click + Generate/Import to create a new secret.
Troubleshoot
If you see the message “You are unauthorized to view these contents” while generating a new secret, follow the below steps:
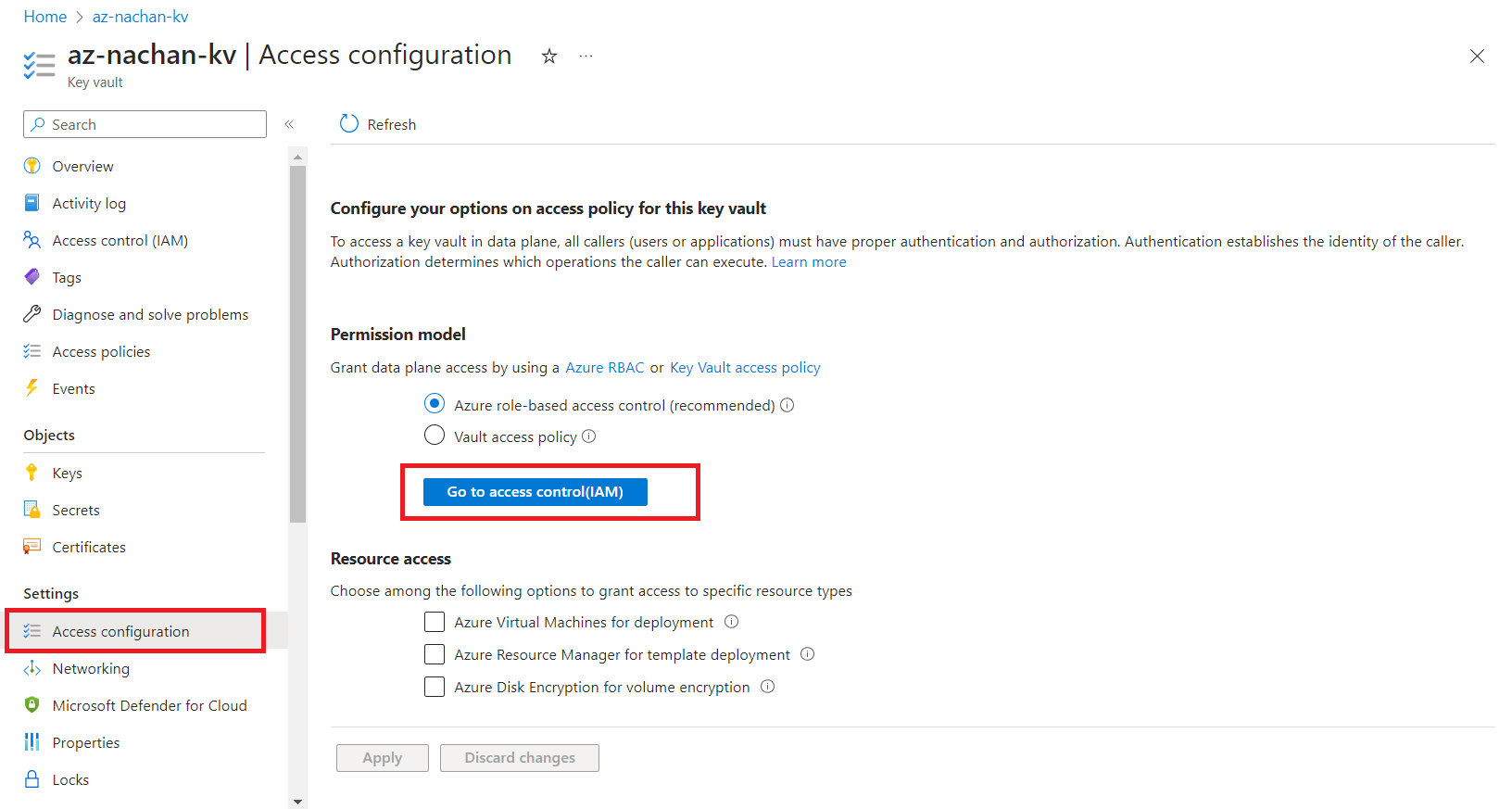
- Under Settings, click Access configuration.
-
Click Go to access control (IAM).
-
Click Add > Add role assignment.
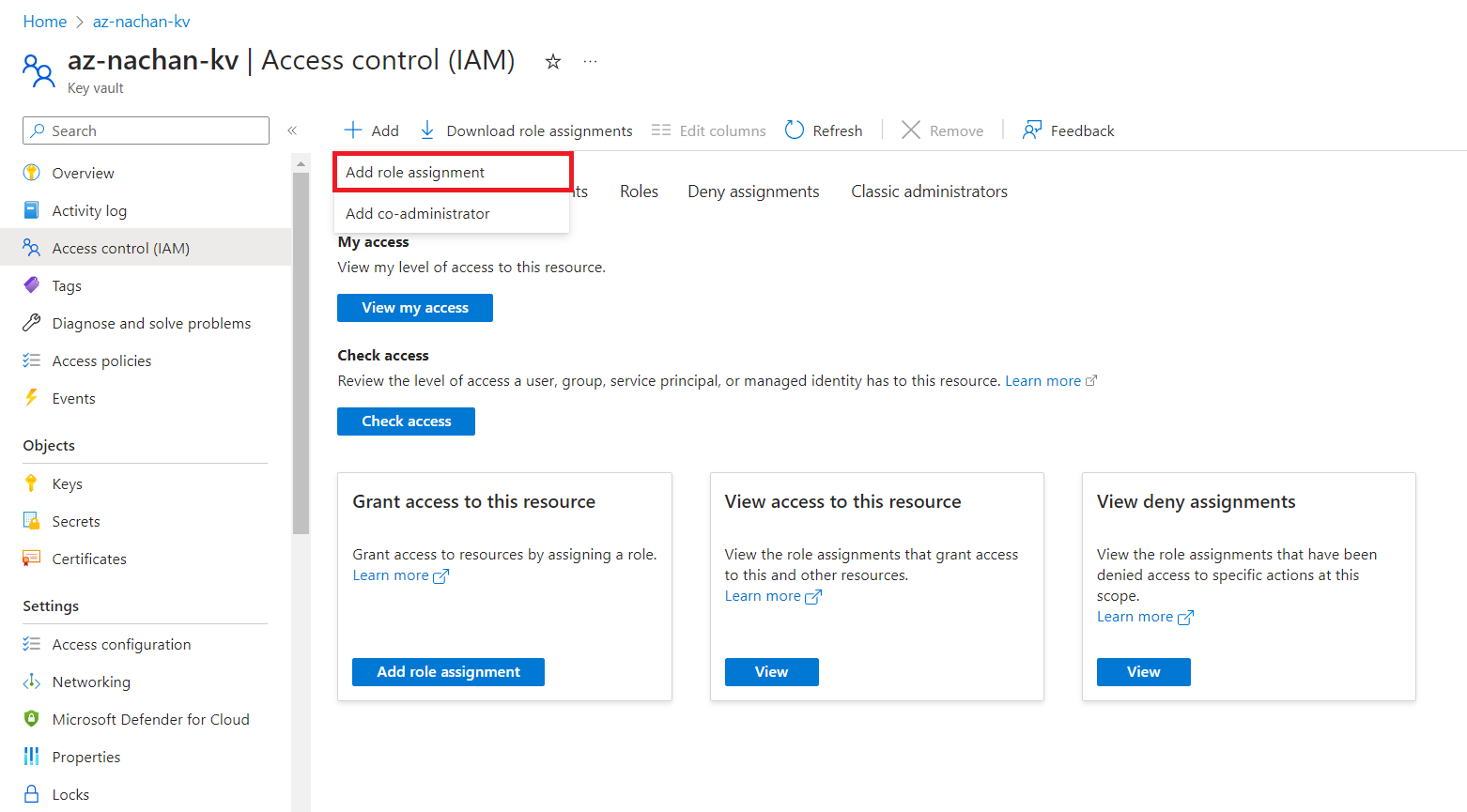
-
Select the appropriate role (e.g., Key Vault Administrator). Add your user as a member and assign the role.
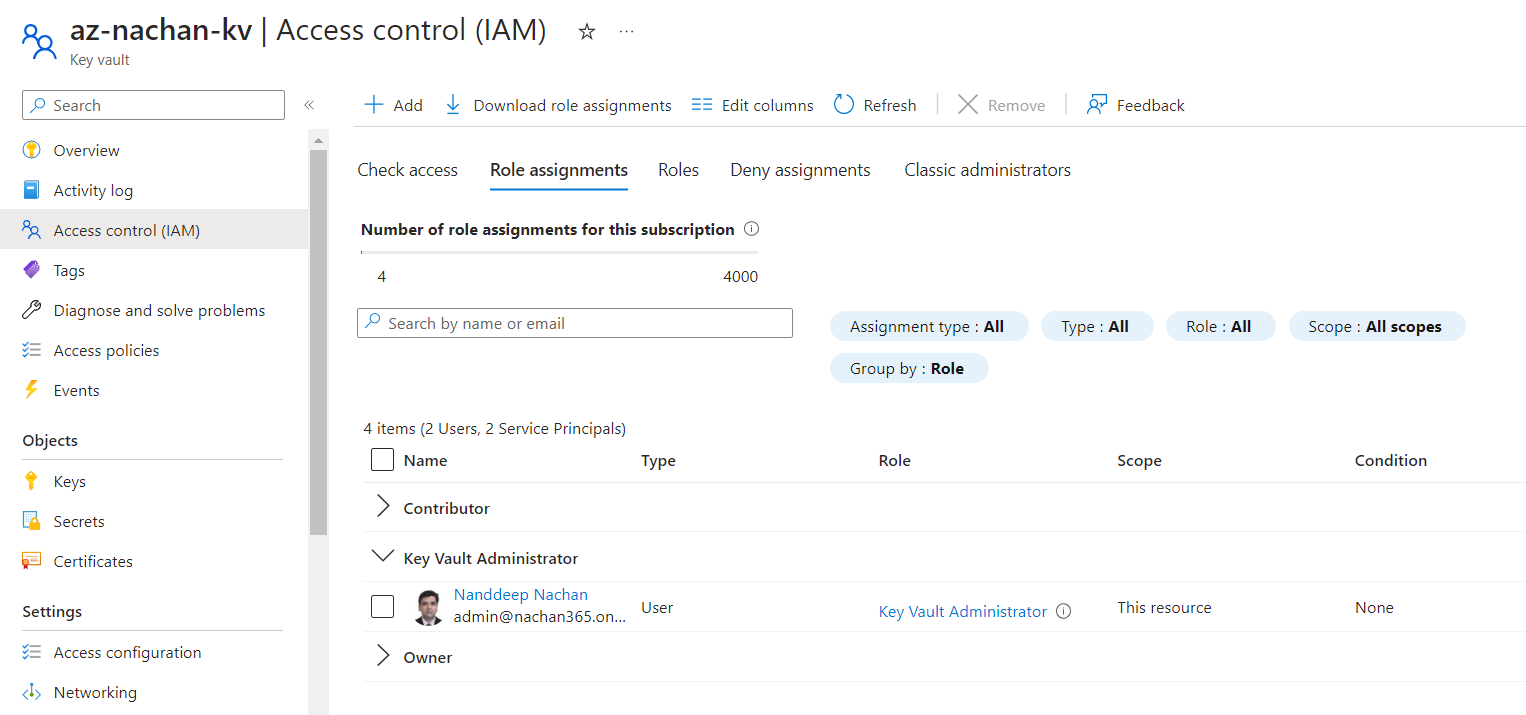
Now, we will maintain the secrets from the key vault using the specified user.
Enable Managed Identity on the Azure Function App
Follow the below steps to enable the managed identity on the Azure Function App:
- Navigate to the Azure Function App.
- Under Settings, click Identity.
- Turn On the System assigned managed identity.
-
Click Save.
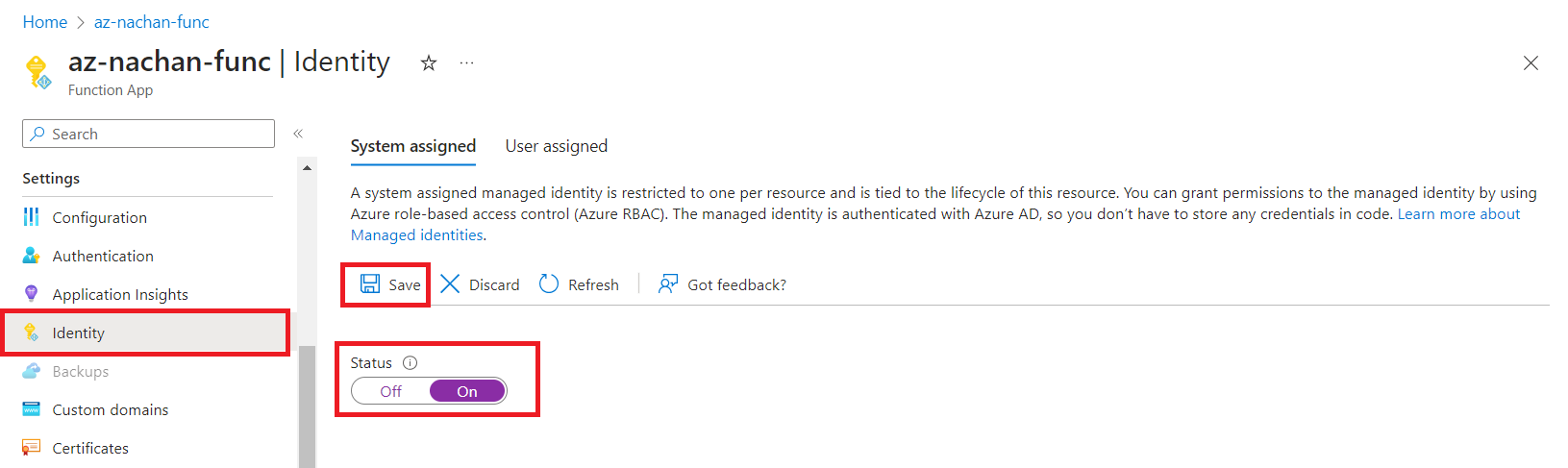
-
Once enabled, click Azure role assignments.
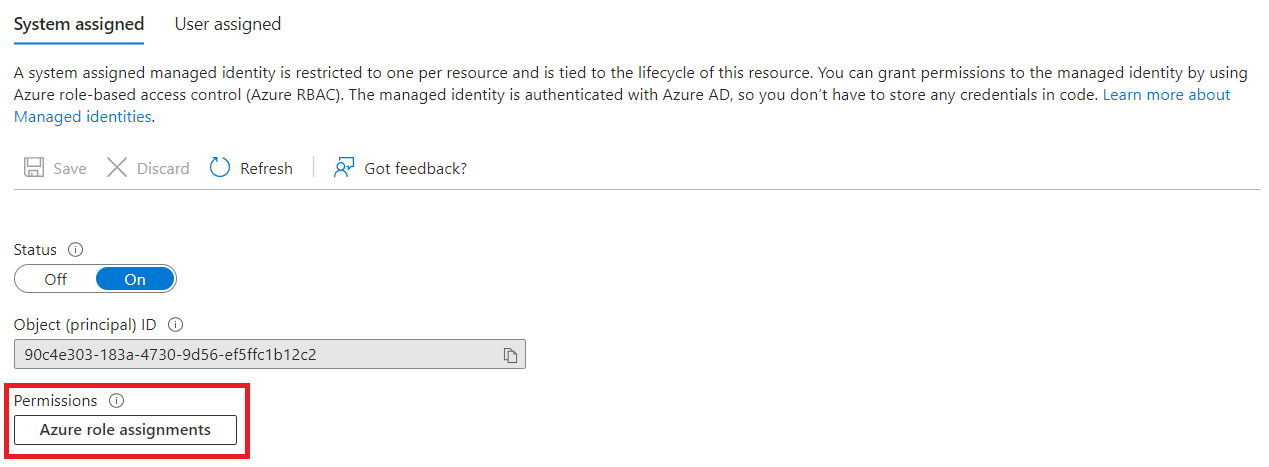
-
Add role assignment as follows.
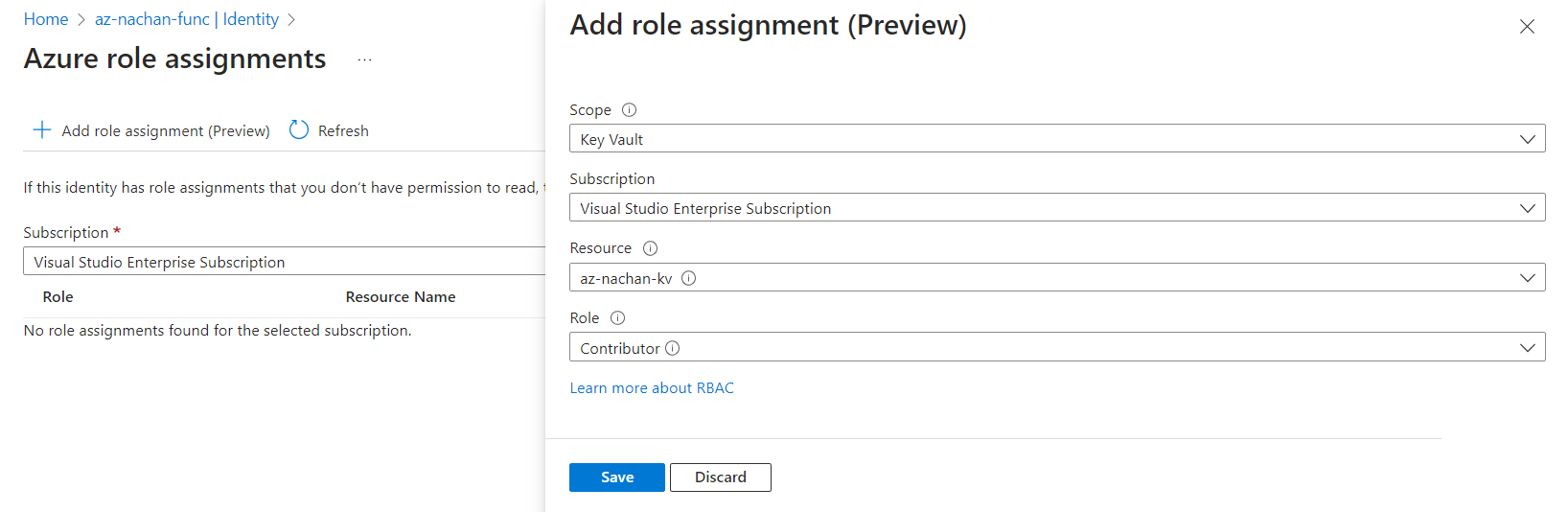
- Click Save.
Now, our Azure function app has a contributor role on the Key vault via managed identity.
Get Secret Identifier from Key Vault
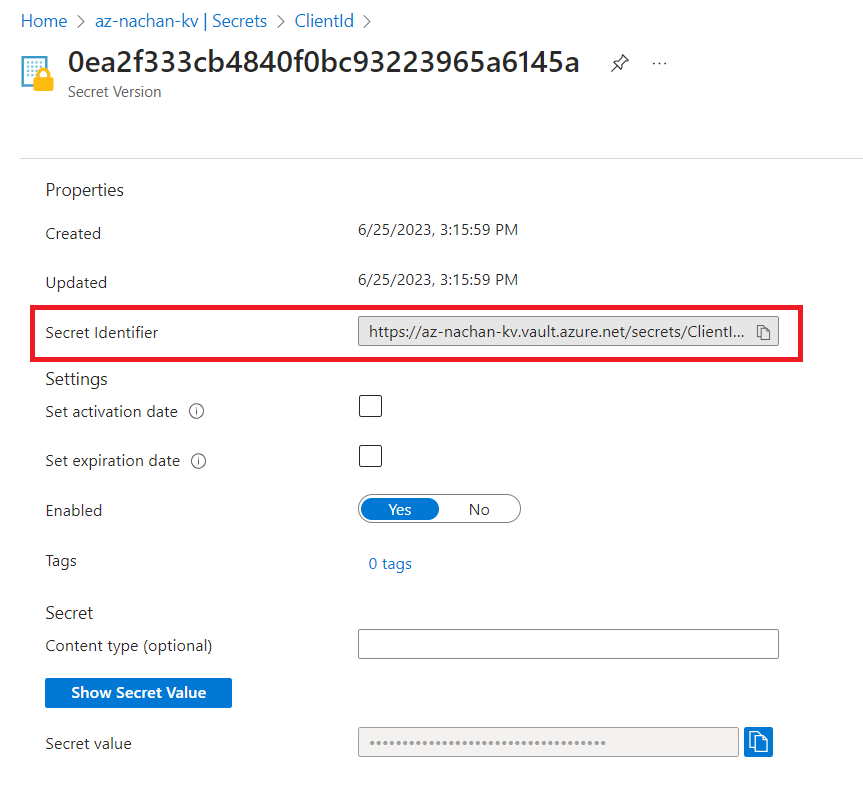
We need to get the Secret Identifier of the secret we have stored in the key vault by the below steps:
- Navigate to the Key Vault.
- Under Objects, click Secrets.
- Select our secret created in the previous step (e.g., ClientId)
- Select the latest version.
-
Note down the Secret Identifier.
Use Managed Identity to access Key Vault Secret
Follow the below steps to use managed identity to access Key Vault Secret:
- Navigate to the Azure Function app.
- Under Settings, click Configuration.
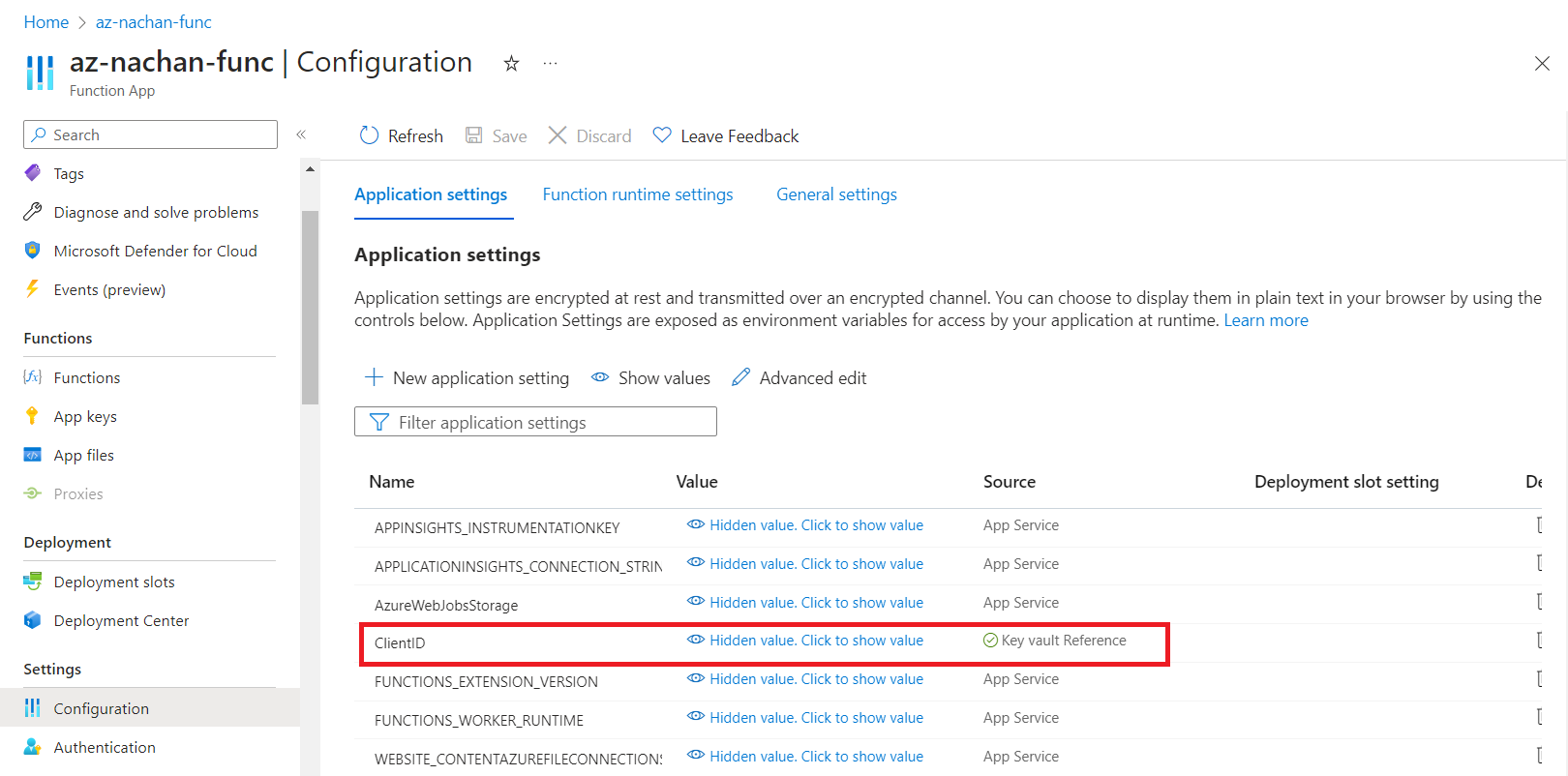
- Edit the ClientId configuration as follows:
@Microsoft.KeyVault(SecretUri=<Secret Identifier>)
Replace the <Secret Identifier> with the Secret identifier from the previous step.
@Microsoft.KeyVault(SecretUri=https://az-nachan-kv.vault.azure.net/secrets/ClientId/0ea2f333cb4840f0bc93223965a6145a)
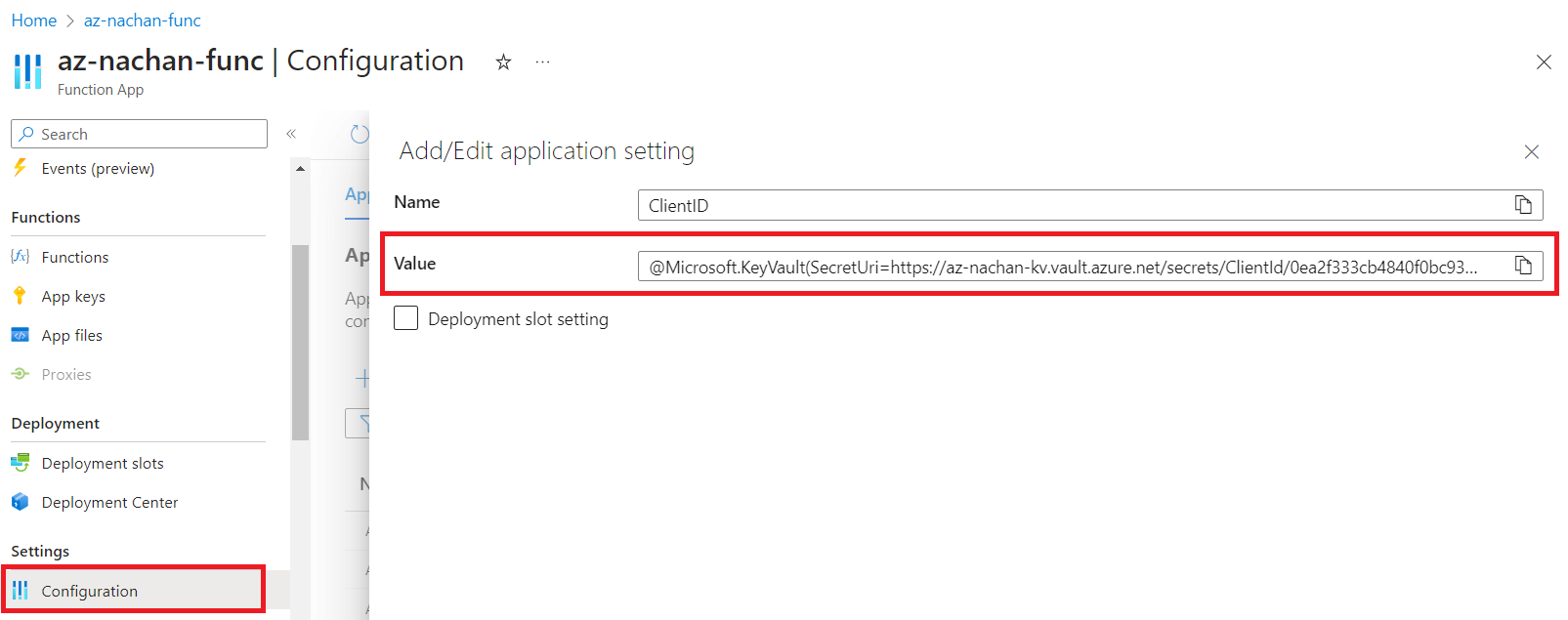
You will see an error for Key Vault Reference.
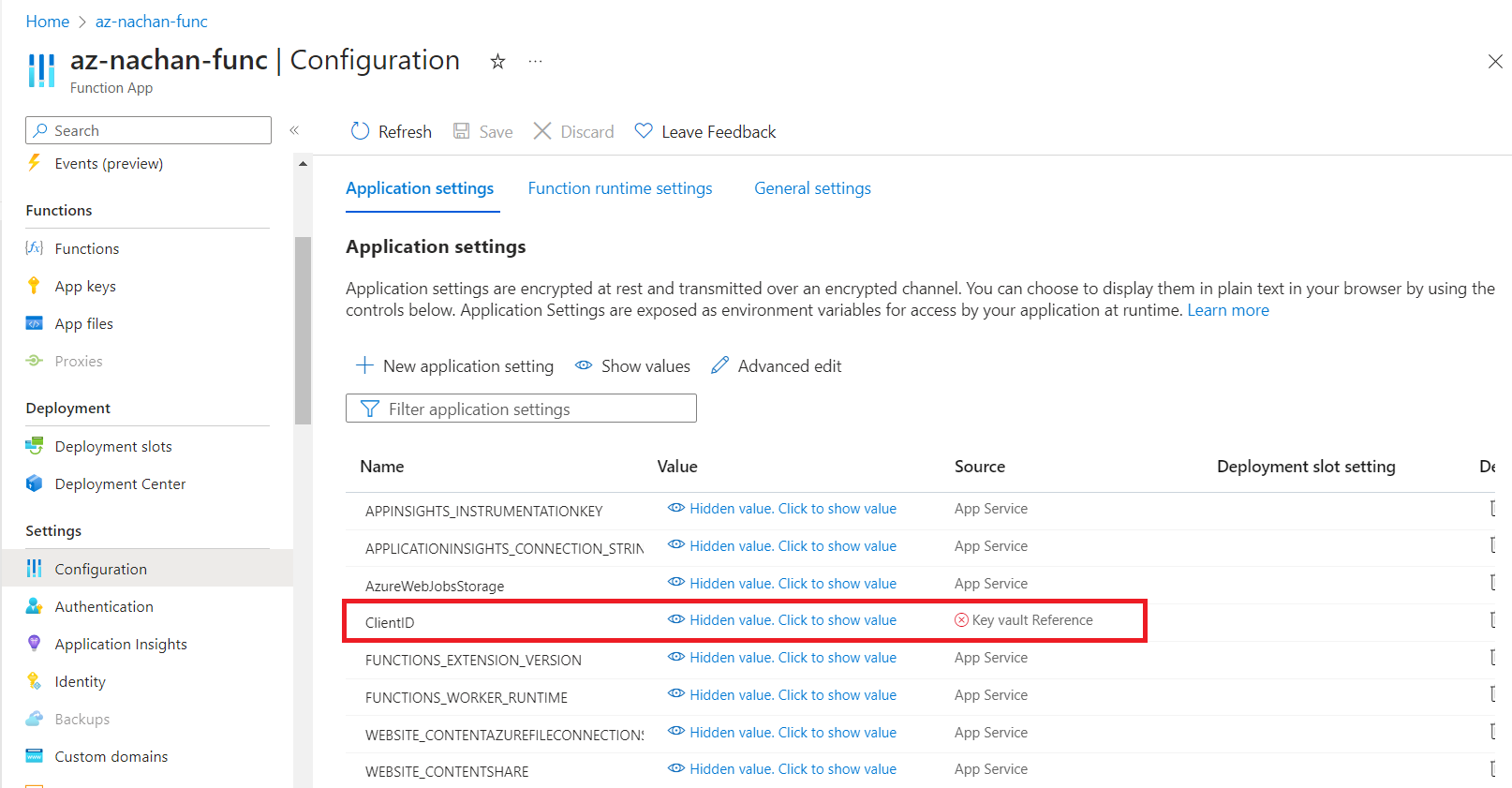
Resolve the error
Follow the below steps to give the Azure function app’s managed identity permission on Azure Key Vault:
- Navigate back to Azure Key Vault.
- Click Access control (IAM).
- Click Add > Add role assignment.
- Select a role (E.g., Key Vault Administrator).
- Under Assign access to, select a Managed identity.
-
Select the Function app’s managed identity.
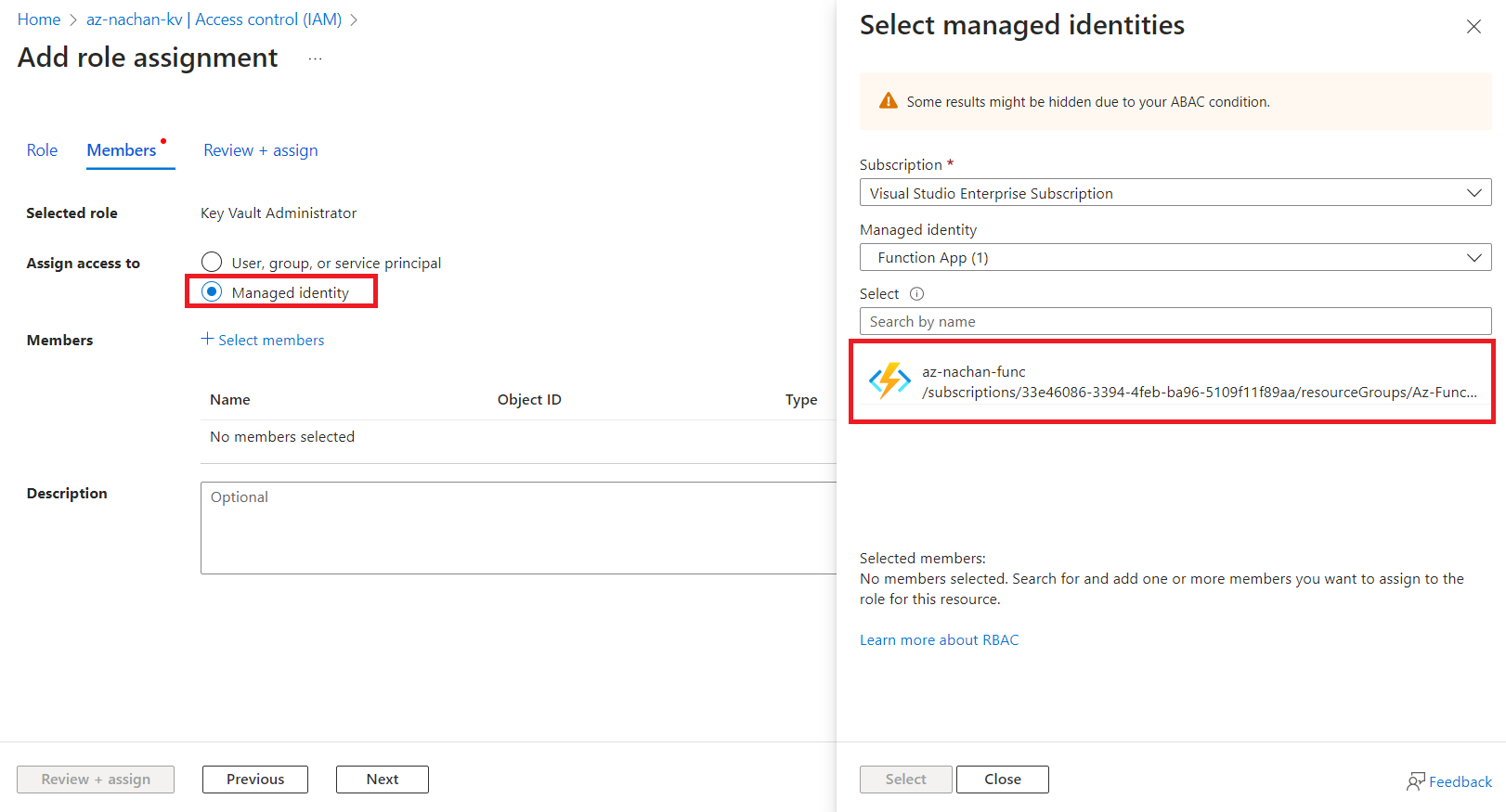
Access Key Vault Secret from Azure Function
Navigate back to the Azure function app and restart it. Now you should see a green tick for Key Vault Reference.

Run the function to validate the secret is being read from the key vault.
Summary
Managed identities provide an effective way to overcome managing secrets for the developers. Azure Key Vault Secret can be read from Azure Function using Managed Identity.


Leave a comment