Manage Conditional Access in Microsoft 365
Overview
Having access to everyone for every app in Microsoft 365 might not be a good idea. Access to each of the apps and services across Microsoft 365 should be restricted in a controlled way. Microsoft Azure’s Conditional Access is helpful in these scenarios.
In this article, we will explore the importance of conditional access and how to use it in Microsoft 365 to control access to the apps.
Why restrict access?
We have to think over whether it is nice to have access to all apps to everyone in the organization, even though an app is not relevant or not being used by them. Restricting access might be helpful in the below scenarios:
- Limit the licensed use of the app.
- Roll out of the service in the organization and be available to pilot users.
- Better assignment of licenses via groups instead of to an individual at random.
- Help secure the app and organization.
What is Conditional Access?
Conditional access is like an if-then statement. If a user needs access to the resource, then they must complete the action.
Apply Conditional Access to Microsoft 365 Apps
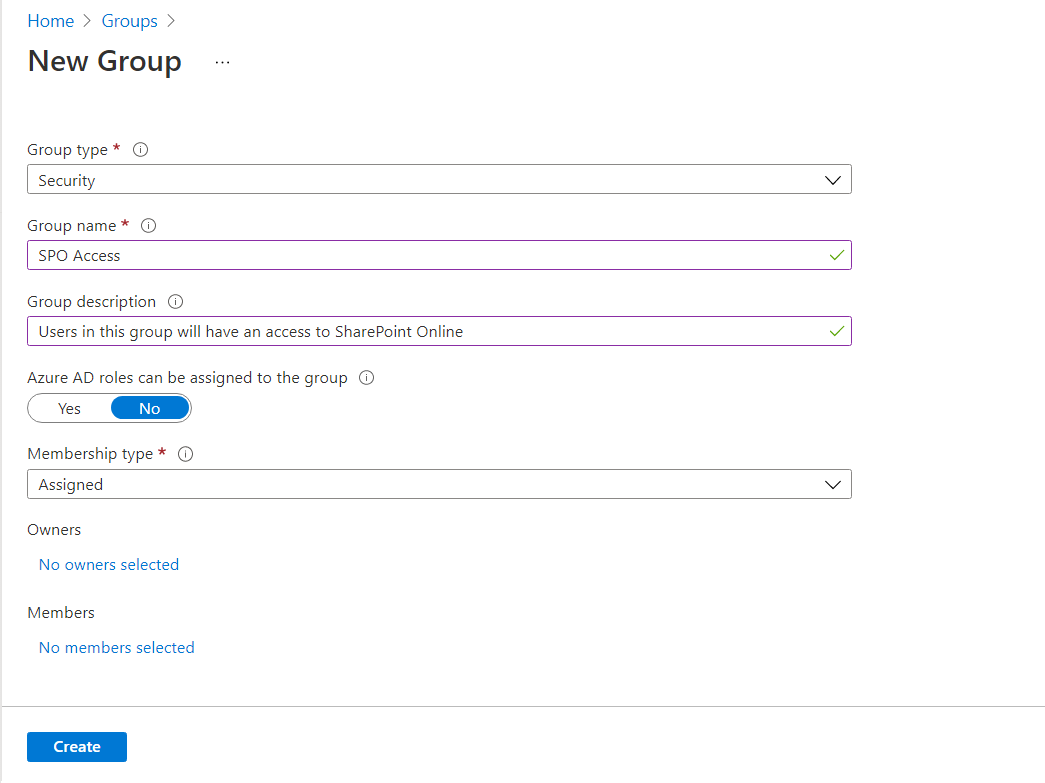
Azure AD Security Group
Consider planning for the Azure AD security group to have access to the app.
Conditional Access Policy
Create a new conditional access policy by following below steps:
- Open MS Azure portal.
- Search for Azure AD Conditional Access.
- Click New Policy > Create new policy.
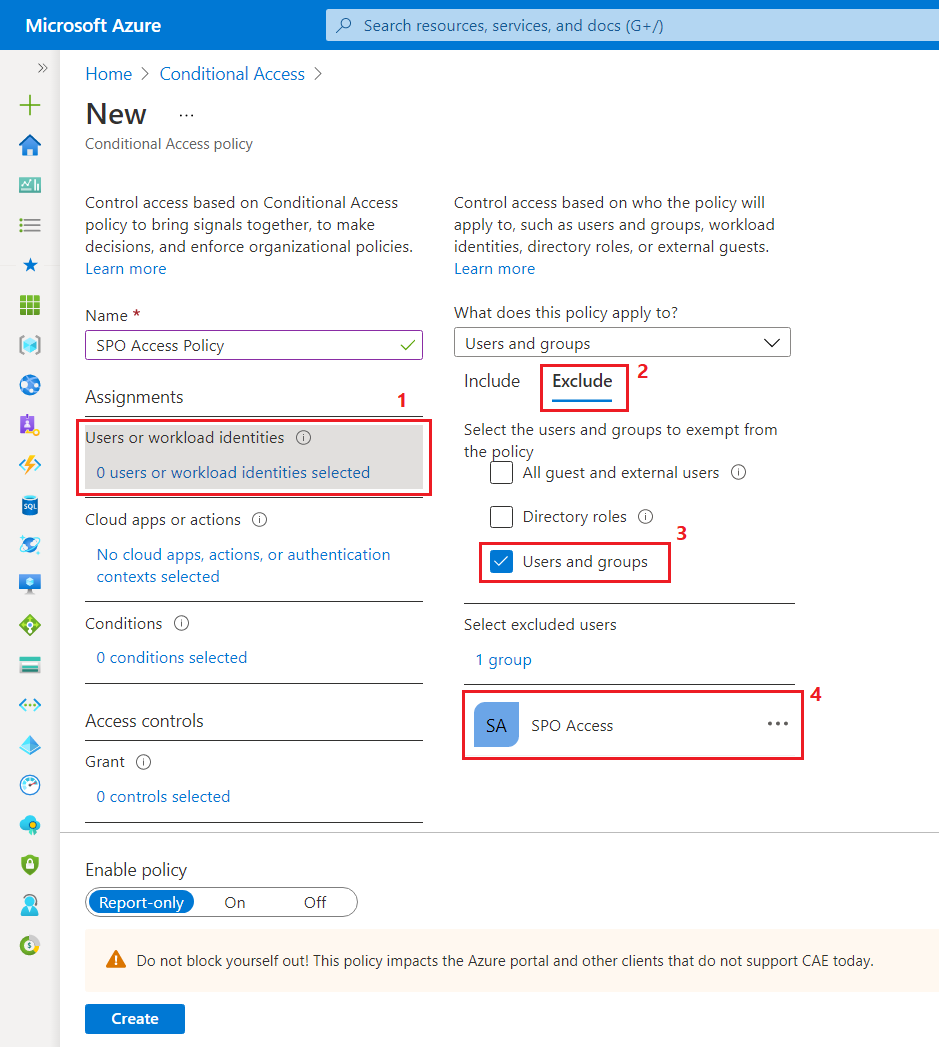
- Specify the name as SPO Access Policy.
- Under Assignments > Users or workload identities , choose to exclude our AAD security group.
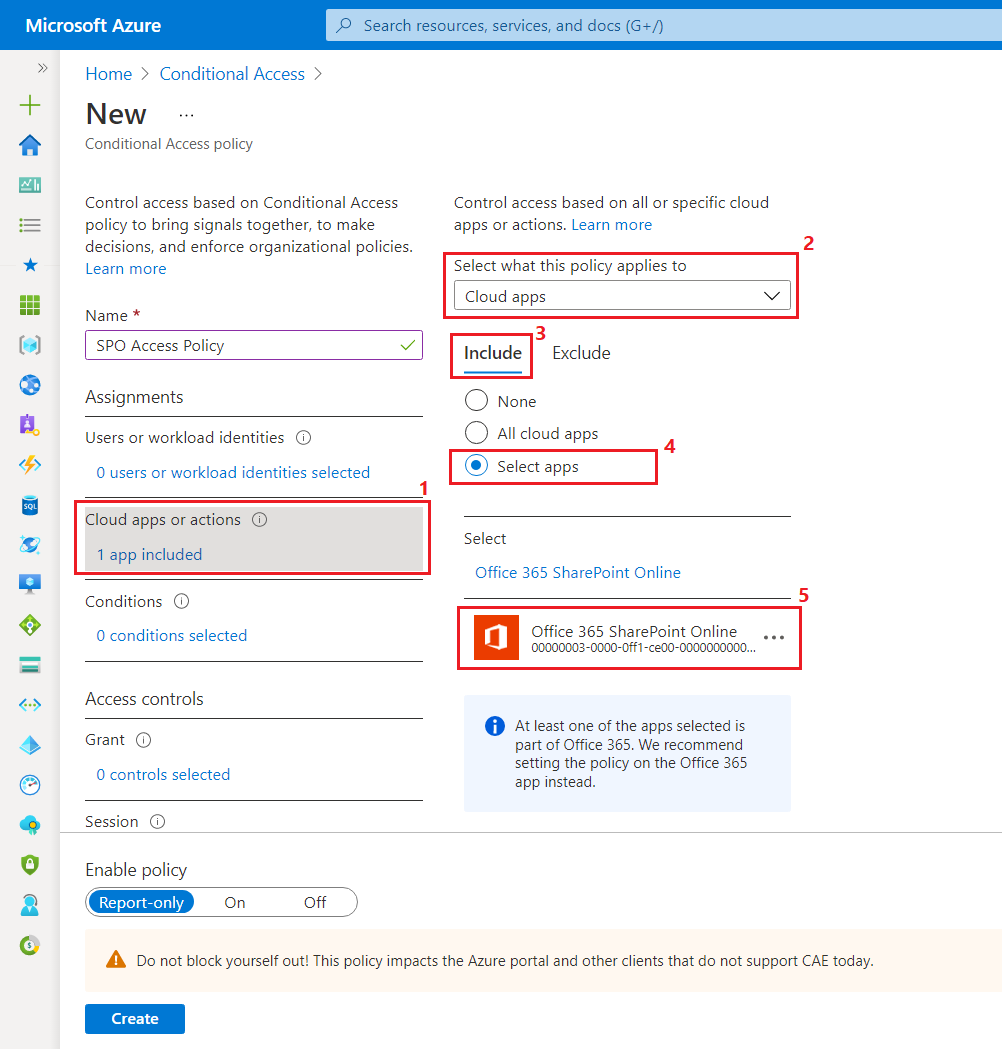
- For Cloud apps or actions, choose the apps to include in the policy. E.g. Office 365 SharePoint Online.
- Under Conditions, choose to include apps as shown below.
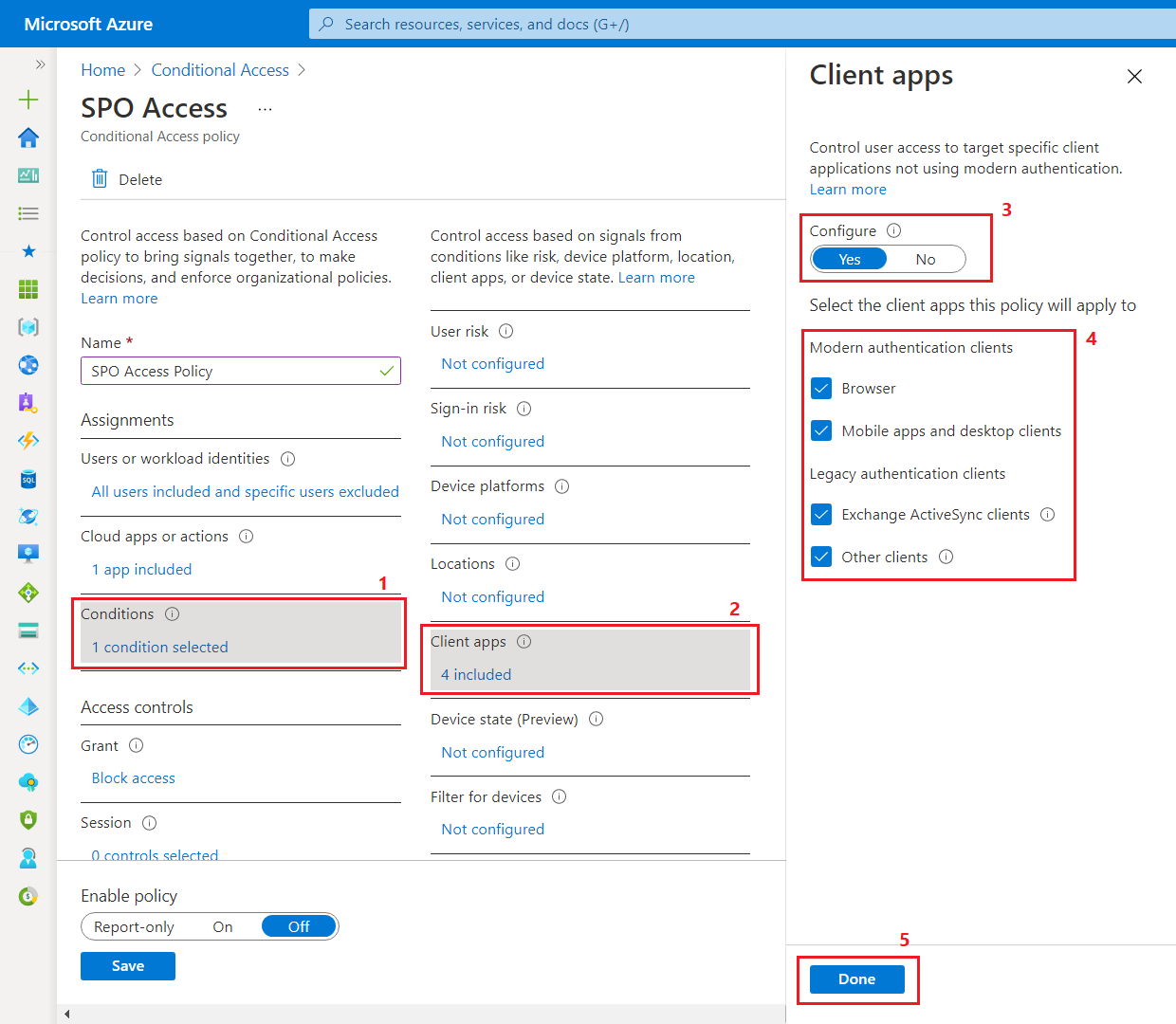
- Under Access Controls > Grant, choose Block Access.
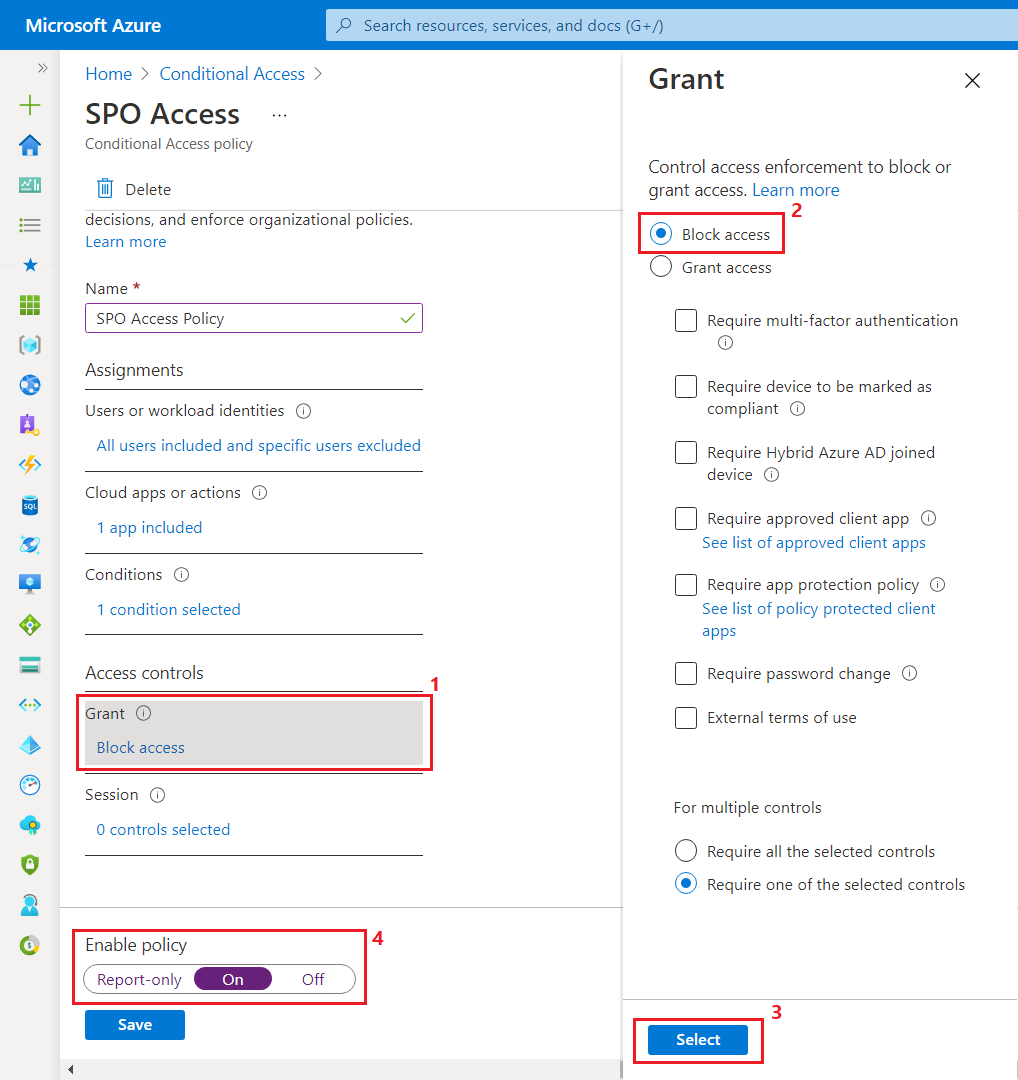
- Enable the policy.
- Click Save.
The policy can be read as "Block access to everyone except AAD security group named SPO Access on SharePoint Online".
Test the Policy
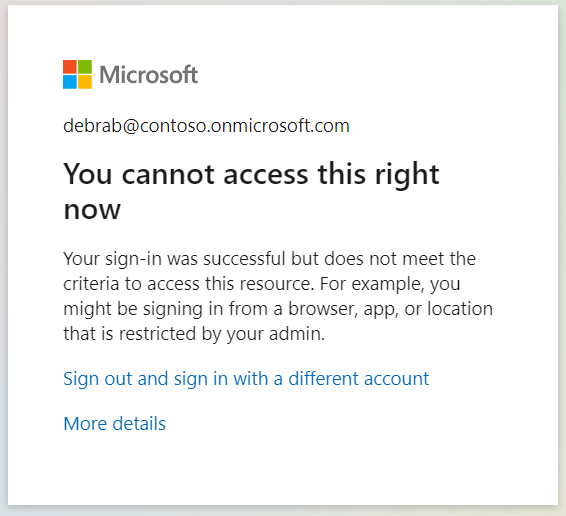
Members of the AAD security group named SPO Access should be able to browse the SharePoint sites. However, non-members should get the below error.

Debug the access issue
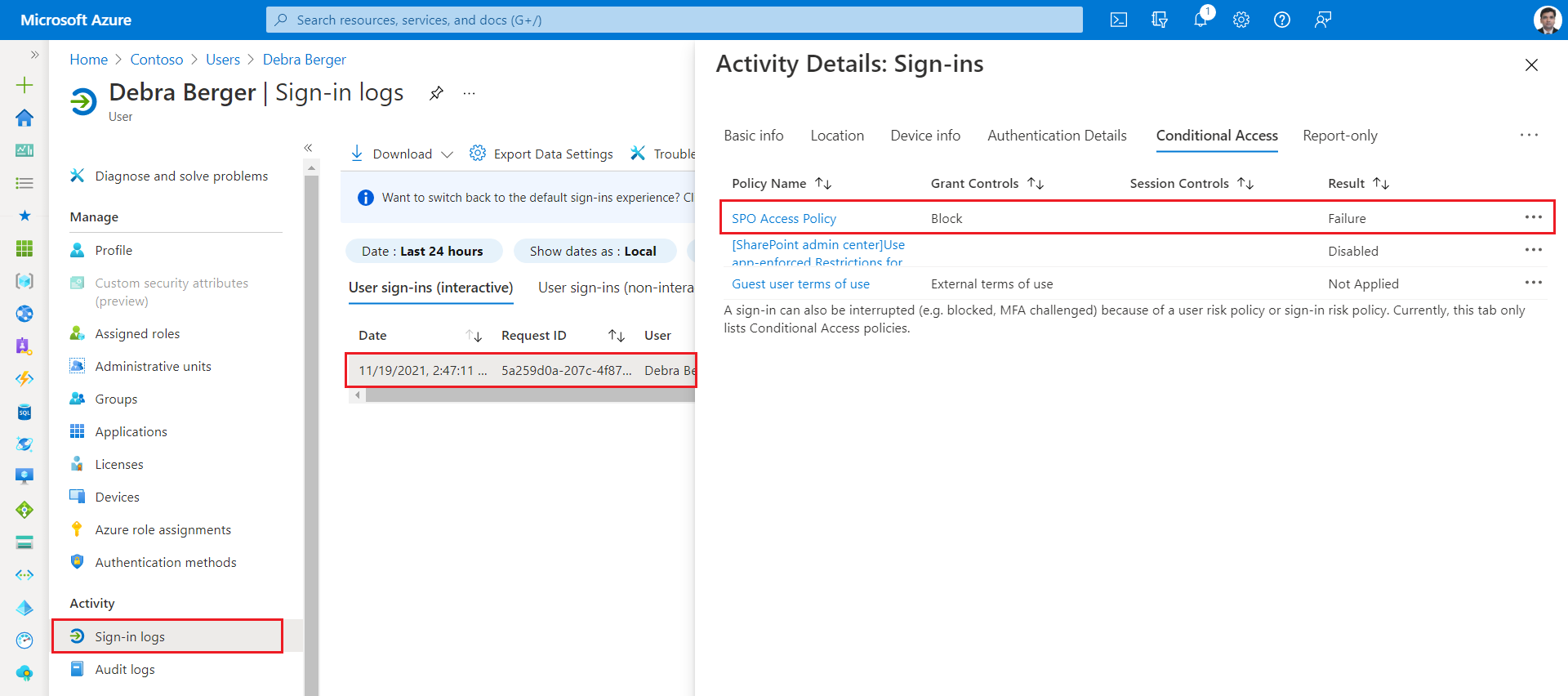
When any of the users are facing an access issue because of the conditional access policy, follow the below steps to find out the root cause:
- Open Azure AD.
- Browse to Users section.
- Search and select the user, facing an access issue.
- Under Activity, click Sign-in logs.
- Locate the one that resulted in a failure.
Summary
Access to each of the apps and services across Microsoft 365 should be restricted in a controlled way. Microsoft Azure’s Conditional Access is helpful in these scenarios.


Leave a comment