Threat detection with Azure Sentinel analytics
Overview
Microsoft Azure Sentinel Analytics provides an intelligent solution to help detect potential threats and vulnerabilities in the organizations.
In this article, we will explore how Azure Sentinel Analytics can help identify and stop cyber attacks.
Azure Sentinel Analytics Overview
Azure Sentinel Analytics helps to detect, investigate, and remediate cyber security threats. It analyzes data from various sources to identify correlations and anomalies. Using analytics rules, we can trigger alerts based on the attack techniques that are used by known malicious actors. With the analytics rule, we can get insights of where an attack originated from, what resources were compromised, potential data lost, along with the timeline for the incident.
The analytics rules can be managed from Azure Sentinel Analysis home page.
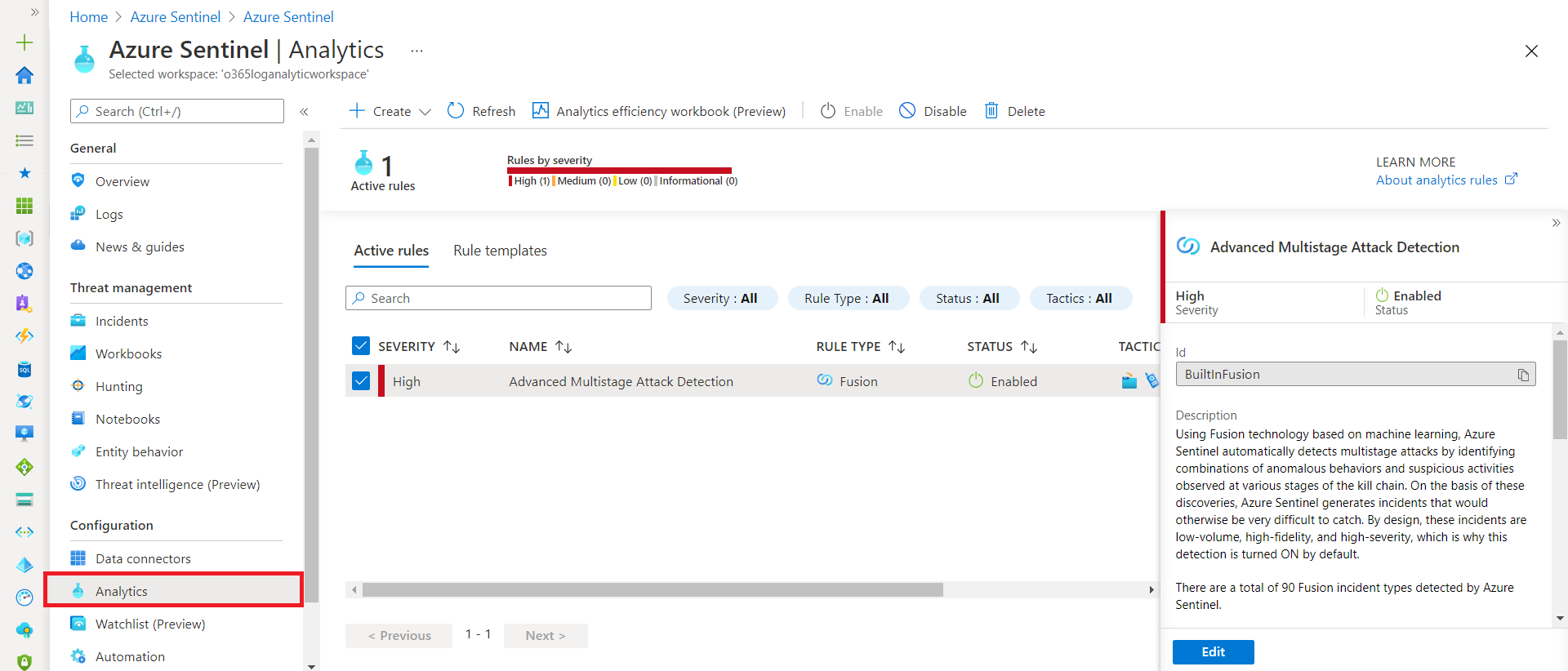
Create Analytics Rule
Alerts triggered in Microsoft security solutions like Microsoft Defender for Identity that are connected to Azure Sentinel do not automatically create incidents. However, we can configure Azure Sentinel to automatically create incidents every time an alert is triggered.
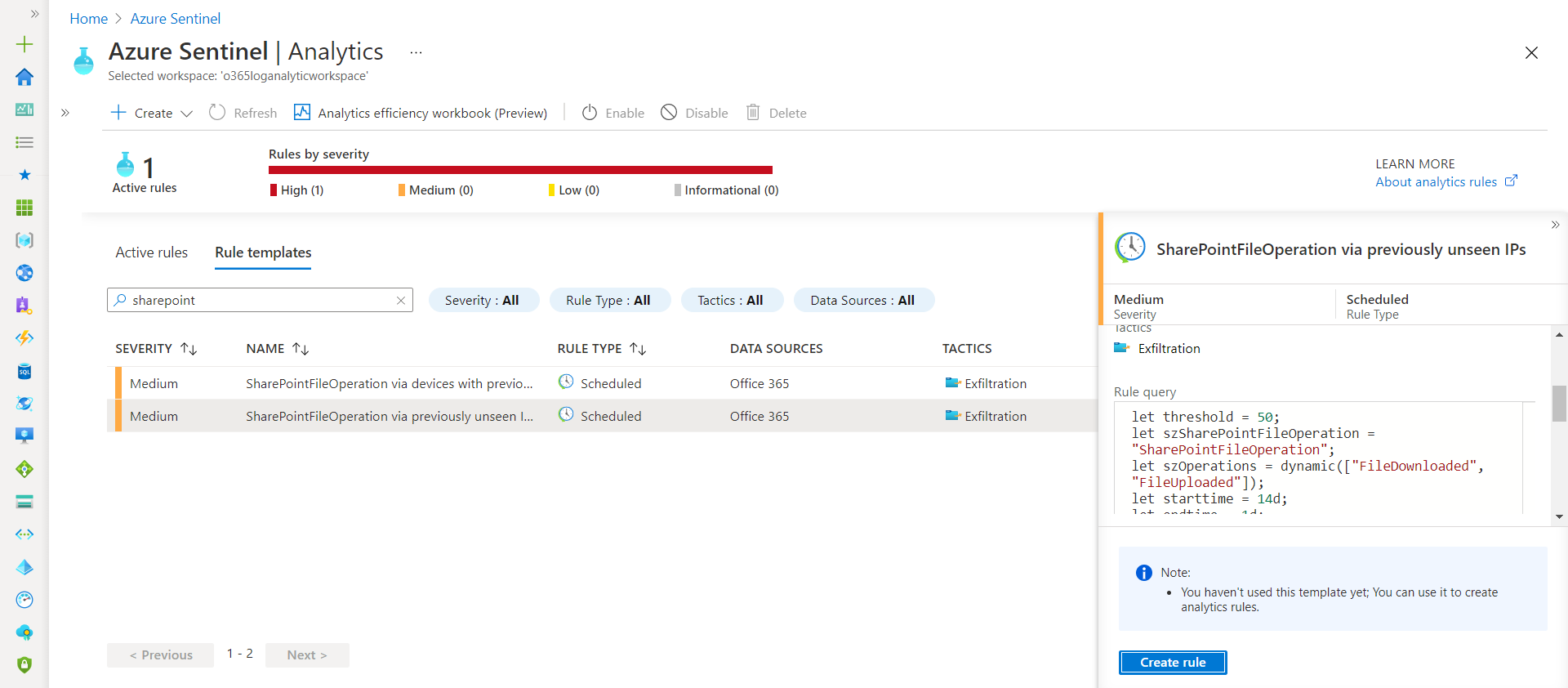
Create rule from Rule templates Follow below steps to create rule from existing built-in templates:
- Select any of existing Rule template.
-
Click Create Rule.
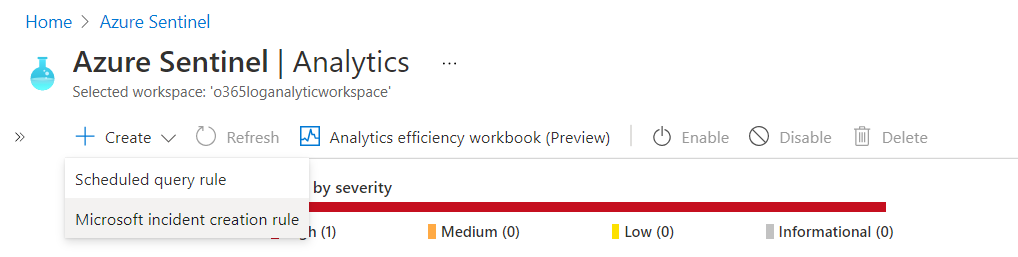
Microsoft incident creation rule We can create a new Microsoft security rule that filters alerts from different Microsoft security services by following below steps:
-
Click Create > Microsoft incident creation rule.
- Specify
NameandDescription. -
Select the
Microsoft security service(e.g. Microsoft Defender for Office 365)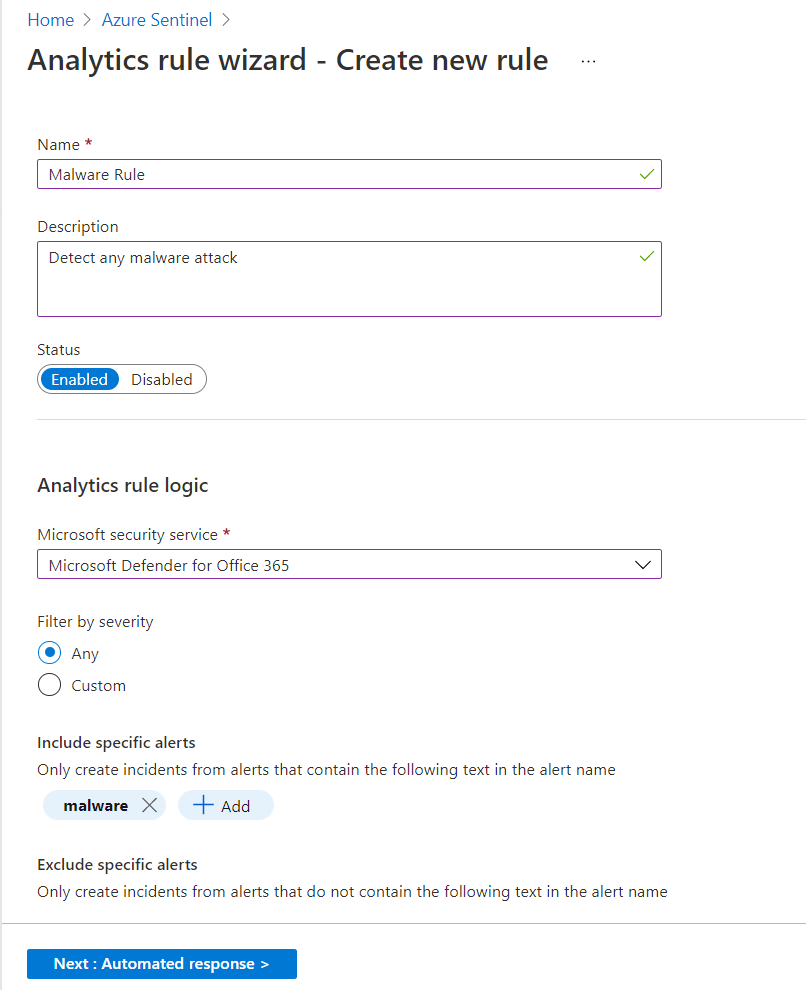
Custom analytics rule with a scheduled query
- Specify unique
NameandDescription. - In the
Tacticsfield, choose categories of attacks to classify the rule. -
Set the alert
Severity.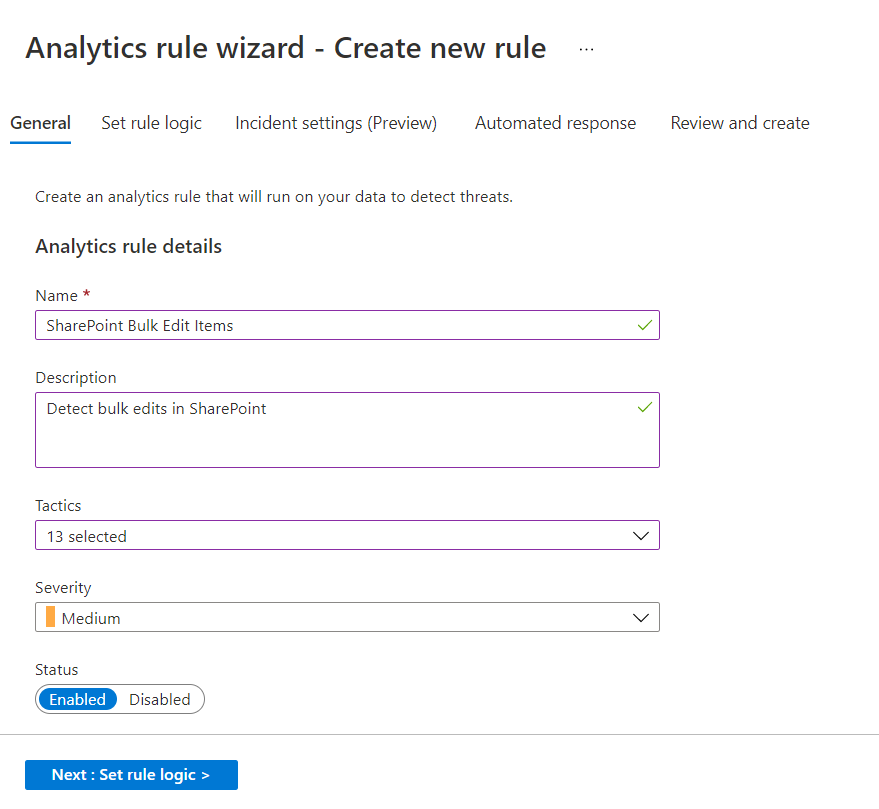
-
Specify
Rule queryas follows:OfficeActivity | where OfficeWorkload in ("SharePoint") and Operation in ("ListItemUpdated")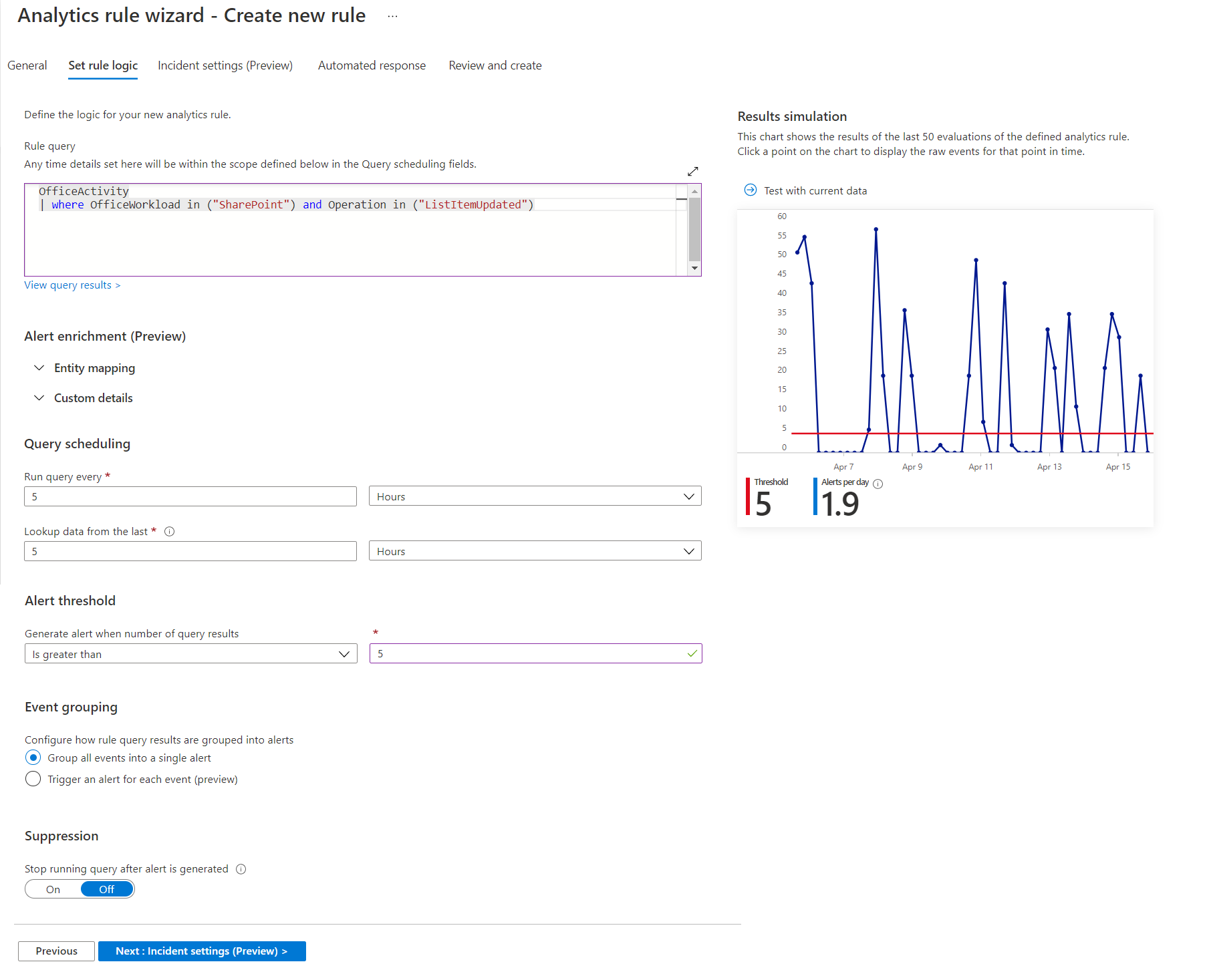
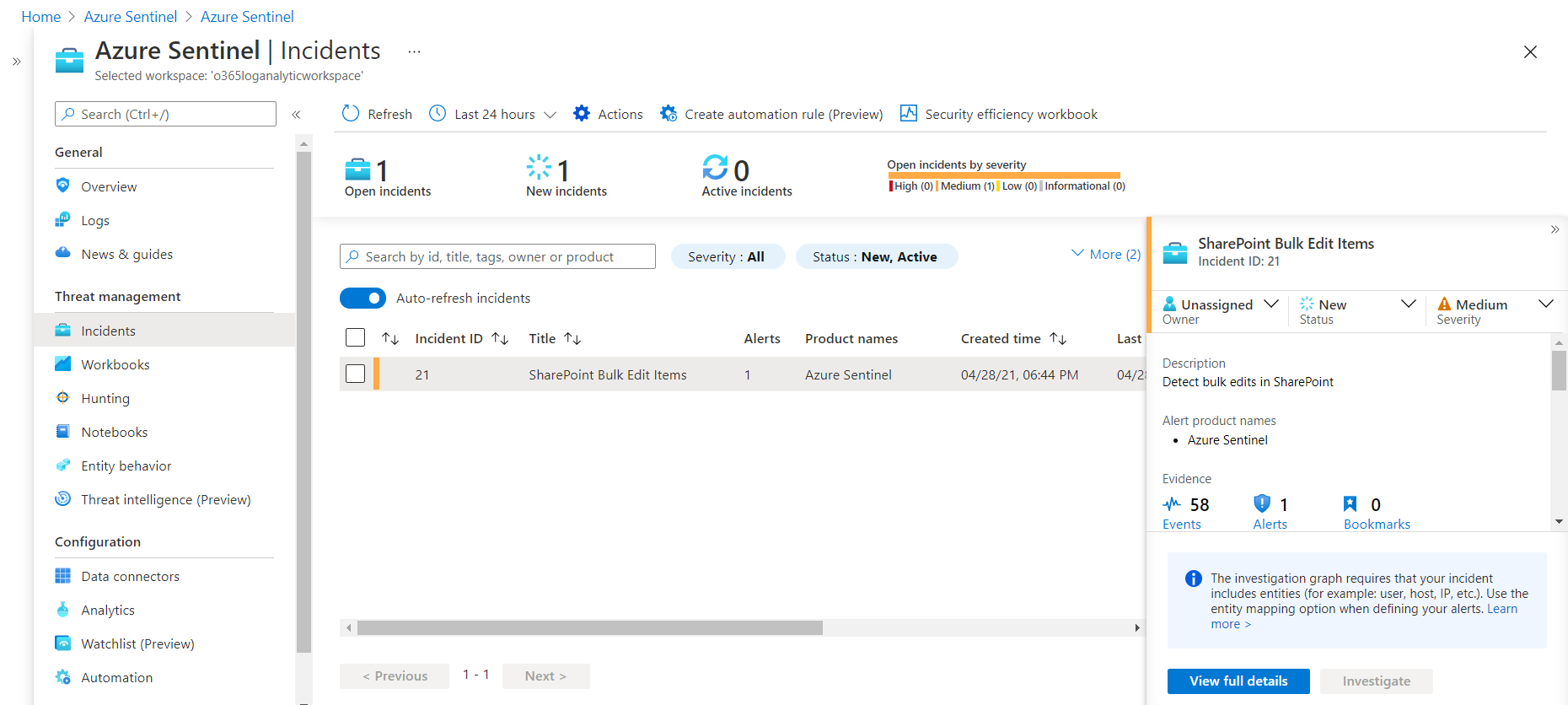
When there will be more than 5 edits to SharePoint list item in span of 5 hours, Azure Sentinel will create an incident for it for bulk editing, as shown below:

Summary
Azure Sentinel Analytics helps to detect, investigate, and remediate cyber security threats by analyzing data from various sources to identify correlations and anomalies.


Leave a comment